What is Locky Ransomware?
After WannaCry and Petya, every other ransomware appears to unfold like wildfire, taking a keep of laptop structures all over the globe, this time it’s being called Locky.
The pc Emergency and response group (CERT) beneath government of India has raised an advisory at the spread of Locky Ransomware via junk mail emails.
Locky could be very just like WannaCry within the way it caused large uproar around the world.
It got here into a photograph in early 2016 and two days ago it became reported that a new wave of spam emails have started circulating again with commonplace to spread editions of Locky ransomware, this time penetrating Indian systems as well. modern-day reports suggest that over 23 million messages have been sent in this marketing campaign.
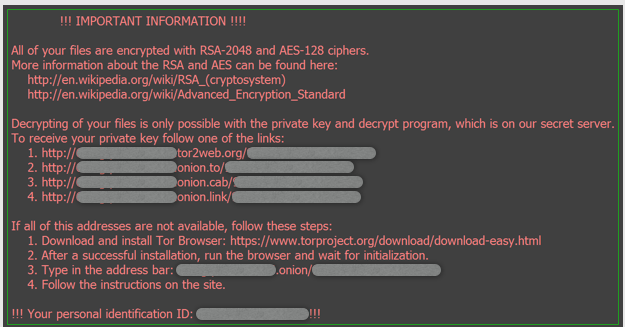
Locky Ransomware strikes your gadget while you least assume it. It locks your pc device and only unlocks it while a ransom demand is paid. Locky makes use of AES( Advanced Encryption Standard) algorithm to encrypt your machine and this is best viable once you download the malicious attachment and permit the Macros settings.
How does it propagate?
The primary mode of spreading of Locky is through junk mail emails. the e-mail consists of commonplace subjects like ‘documents’, ‘please print’, ‘photo’, ‘pictures’, ‘pictures’ and ‘scans’ which may additionally exchange relying at the target audience. when you open this electronic mail, and click on on the attachment variants of the ransomware routinely get downloaded on your laptop.
As soon because the editions are downloaded, your desktop historical past is changed with commands to be observed and indicates a ‘.htm’ a document named “Lukitus[dot]htm”.
as soon as the system is infected with the aid of Locky, all files are encrypted and string with random numbers with extension ” [.]lukitus” or “[.]diablo6” is appended to the encrypted files. Lukitus is French for ‘locking’.
The commands contain set up of TOR browser (Onion Router network) and touring “.onion” web sites. The users are then demanded to pay 0.5 Bitcoins to avail this decryption provider that’s equivalent to almost Rs. 1.five lakh (INR).
furthermore, it’s been pronounced that an unsolicited email marketing campaign displaying links to fake Dropbox websites is getting used to spread Locky variations. If the pages are considered in Chrome or Firefox, they show a fake notification declaring “you don’t have the HoeflerText font”. those faux notifications had an “replace” button that returns a malicious JavaScript (.js) file. [1]
In a nutshell, what it does is that this:
You obtain an e-mail, with an attachment that once opened is a scrambled mess of phrases.
on the pinnacle are the phrases, ‘enable Macros if the facts encoding is wrong.’
the instant you enable macros, in place of correcting the document, your system gets encrypted and Locky ransomware is activated and home windows potential to take stay backup known as Shadow copies is also compromised.
Your wallpaper modifications to ‘how to decrypt’ message showing photograph.
Recommendation against Locky:
here’s a listing of guidelines counseled to the users to save you Locky from compromising your pc.
- The most recommendation to customers is to not to open any unsolicited mail emails, or attachments as well as update anti-unsolicited email and block lists.
- Block malicious IP addresses.
- Do not download or open attachments which incorporate Zip documents.
- perform an ordinary backup of your data, and shop it on a few different gadgets maximum preferably offline.
- Disable Macro in Microsoft workplace programs ‘Disable all macros with notification’. Macros can run in Ms. Office applications best if the Macro settings are set to ‘permit all macros’ or if the person manually allows it. this is done so due to the fact the email attachment is available in Macro-Enabled shape.
- Have an updated Antivirus hooked up on your non-public in addition to workplace systems
- Don’t click on pointless popups at the same time as visiting websites which can also include Embedded JavaScript (.js) report that could download the ransomware.
- Don’t use administrative accounts for wearing out business as ordinary sports, which limits the rate of set up. additionally, disable far flung Desktop Connections.
- Don’t go to malicious websites or blocked websites listed at the advisory at least.
- Replace your running structures, third-party packages like browser, browser plugins and anti-virus software for modern-day protection patches.
- practice all of the above encouraged. no matter this, in case you suspect your pc gadget has been inflamed, contact your IT team and not at all pay any ransom.
Generic Prevention Tools:
- Tool (NoMoreCry) to prevent Wannacry Ransomware by CCN-CERT:
https://loreto.ccn-cert.cni.es/index.php/s/tYxMah1T7x7FhND?path=%2F20170513%20CCN-CERT%20NoMoreCry%20Tool - Sophos: Hitman.Pro
https://www.hitmanpro.com/en-us/surfright/alert.aspx - Bitdefender Anti-Crypto Vaccine and Anti-Ransomware (discontinued)
https://labs.bitdefender.com/2016/03/combination-crypto-ransomware-vaccine-released/ - Malwarebytes Anti-Ransomware(formally Crypto Monitor)
https://blog.malwarebytes.com/malwarebytes-news/2016/01/introducing-the-malwarebytes-anti-ransomware-beta/ - Trendmicro Ransomware Screen Unlocker tool:
https://esupport.trendmicro.com/en-us/home/pages/technical-support/1105975.aspx - Microsoft Enhanced mitigation and experience toolkit(EMET)
https://www.microsoft.com/en-us/download/details.aspx?id=50766
For More details, Source : http://www.cyberswachhtakendra.gov.in/alerts/locky_ransomware.html























Leave A Comment